CBEST Implementation Guide: What’s New In 2024
Published on March 20, 2024 by SECFORCE
As UK financial services firms will know, the Critical National Infrastructure Banking Supervision and Evaluation Testing (CBEST for short) is an intelligence-led security testing framework.
Designed in 2014 by the Bank of England to help financial services firms and financial market infrastructures (FMI) understand their defence capabilities, CBEST involves cyber threat intelligence and attack simulations that mimic the actions of real-world attackers.
For those who have to (or want to) participate in CBEST, the CBEST Implementation Guide covers all aspects of the process.
Recently, the Bank of England Prudential Regulation Authority updated this guide. So, what changed? Luckily, not that much.
The core technical practices remain the same, with a few small (mostly clarifying) additions and a revamped structure.
Read the blog below for a refresher on the overall CBEST process and a quick summary of the changes.
When should CBEST take place?
CBEST can take place when a firm/financial market infrastructure (FMI):
- Wants to do so voluntarily as part of its resilience program.
- Is requested to do so by a regulator. The PRA and FCA will regularly agree on a list of those who need to be assessed in line with the thematic focus and supervisory strategy.
- Experienced an incident or other event that made the regulator request a CBEST.
What changed: Previously, the PRA and FCA agreed on a list of organisations to be assessed triannually rather than “regularly.”
Stakeholders
The following stakeholders take part in a CBEST assessment:
- Regulator.
- Control Group (CG) of the participant firm/FMI, i.e., a select number of senior individuals who will manage and oversee the CBEST assessment.
- Threat Intelligence Service Provider (TISP).
- Penetration Testing Service Provider (PTSP).
What changed: In the previous iteration of the guide, the National Cyber Security Centre (NCSC) was listed among the stakeholders involved in a CBEST assessment and featured more prominently throughout the guide.
Another change in the updated version of the CBEST guide is that there are now nine bullet points (aka responsibilities) instead of eight under the list of CG's responsibilities.
The new 9th bullet point states that CGs need to report to the regulator immediately any “significant concerns” about their project plan (like delays) and the technical execution of threat intelligence and penetration testing phases.
The final bullet point under CG’s list of responsibilities also clarifies that deliverables must be shared with the regulator unredacted (unless otherwise required). The previous iteration of the guide only said deliverables must be shared on a timely basis.

CBEST timeline
The CBEST process is divided into four phases (more on these below). The different phases usually overlap, but the CBEST Implementation Guide has an indicative timeframe for each one.
Importantly, timeframe indication shouldn’t serve as a pre-set plan so as not to limit the assessment.
What’s changed: The updated version of the guide says the typical CBEST project duration is between 9 and 12 months (9 months in the previous version).
Risk management
It’s up to the CG to ensure the CBEST assessment is conducted in a controlled manner, identify risks, and implement mitigating actions. These mitigating actions also need to be regularly reviewed and updated.
The Penetration Testing (PT) phase specifically needs careful consideration.
The CG can temporarily stop the CBEST assessment if there are concerns over damage or potential damage to a system or if there’s disruption to an important business service (IBS).
Before the CBEST starts, the CG should complete a CBEST risk assessment.
What’s changed: The updated version specifies that the risk assessment process needs to ensure the CG is in technical and operational control during all CBEST phases.
According to the updated guide, your CBEST risk assessment needs to consider external impacts and internal dependencies and assumptions that could impact any of the phases.
CBEST process
There are four phases in a CBEST assessment process:
Phase 1
Also known as the Initiation Phase, this is when the CBEST assessment is launched.
The scope is established, and the firm starts to procure a Threat Intelligence service provider (TISP) and Penetration Testing Service Provider (PTSP).
This phase is further divided into four sub-phases:
- Launch. The regulator sends a firm/FMI a CBEST notification letter. The firm/FMI starts to prepare for CBEST in line with the CBEST implementation guide. Meanwhile, the regulator drafts the initial CBEST Scope Specification document outlining the IBSs that must be tested. The implementation guide also includes details on cross-jurisdictional assessments.
- Engagement. The regulator meets with the firm/FMI to discuss the CBEST process, who will be involved, and their responsibilities. The regulator also draws up legal clauses that the firm/FMI considers.
- Scoping. The regulator and CG agree on the scope in the CBEST Scope Specification document.
- Procurement. The firm/FMI procures and onboards CBEST-accredited TISP and PTSP.
What’s changed: The updated version of the guide adds a new bullet point to the list of things to be discussed by the firm/FMI and the regulator in the Engagement part of phase 1, “Objectives of the CBEST.”
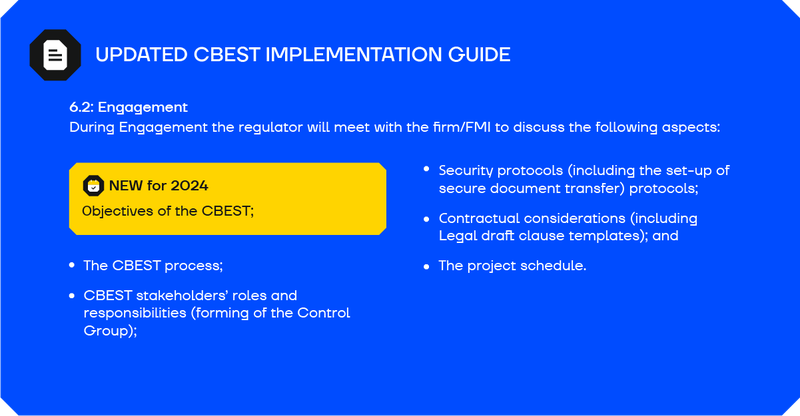
Under the legal clauses section (engagement), the updated guide now also states that firms/FMIs need to ensure reports are not redacted unnecessarily.
Phase 2
The Threat Intelligence phase. Threat intelligence deliverables are produced during this phase, and threat scenarios are developed.
The Threat Intelligence phase is further divided into four sub-phases:
- Direction. The TISP produces an IBS-focused Threat Intelligence Plan, and the CG updates the Project Initiation Document (PID) based on this plan. The CBEST guide lists what the TISP needs for efficient intelligence gathering.
- Intelligence. The TISP collects, analyses, and disseminates IBS-focused intelligence related to targeting (attack surfaces) and threat intelligence (threat actors and scenarios). The TISP then develops scenarios and drafts a Penetration Test Plan.
- Validation. During a validation workshop, the TISP provides an overview of the Targeting Report and Threat Intelligence Report, and the PTSP presents a draft Penetration Test Plan. Regulators provide feedback, and the reports are revised as needed.
- Assessment. The TISP performs a Threat Intelligence Maturity Assessment on the firm’s/FMI’s internal TI function.
What’s changed: The updated guide highlights the importance of the TISP and PTSP working together. They are both supposed to agree on the scenarios' operationalisation and describe detailed technical outcomes and activities on how threats are emulated and what security controls and capabilities are targeted.
There’s also a new bullet point under the reporting process in the Intelligence phase. This states that the final reports (Threat Intelligence Report and the Targeting Report) can’t be shared beyond the CG within the firm until the CBEST is over.

The updated report also no longer mentions NCSC.
Phase 3
The Penetration Testing Phase. The firm’s systems and services are pen tested, and its threat intelligence maturity and detection and response abilities are put to the test.
The Penetration Testing phase is further divided into four sub-phases:
- PT Planning. The PTSP produces a final Penetration Test Plan and a Penetration Test Risk Management Plan.
- Execution. The PTSP carries out an intelligence-led Penetration Test.
- Assessment. The PTSP assesses the firm’s/FMI’s detection and response capabilities.
- Review. A Review workshop takes place. The CG, PTSB, TISP, and regulator review the draft Penetration Test Report, TI findings and recommendations, TI maturity assessment, and D&R Capability Assessment.
What’s changed: Nothing.
Phase 4
The Closure phase. The firm/FMI drafts and then finalises its Remediation Plan and regulators review its implementation.
The Closure phase is further divided into three sub-phases:
- Remediation. The CG drafts a Remediation plan, which it shares with the regulator.
- Debrief. Representatives from the TISP and PTSP meet with the regulator to discuss what activities/deliverables and aspects of the CBEST process went well and what could be improved.
- Supervision. The regulator assesses the implementation of the CBEST Remediation Plan. The firm/FMI has to give updates and confirmation when it completes remediating actions.
What’s changed: Under the Remediation sub-phase, there’s a new paragraph describing what the final Remediation Plan needs to capture.
Specifically, the firm being tested needs to assess the risk and impact of the technical findings from all phases of CBEST on its business. The plan should also cover who is responsible for remediation and what technical activities have been agreed on. Any lessons learned from CBEST should be used to help figure out if similar problems might exist in other areas that weren't tested.
Post CBEST: Thematic analysis
The regulator produces a periodic thematic report based on all the CBESTs that happened in a particular period. To improve industry-level cyber resilience, an anonymised report is shared with non-CBEST firms/FMIs. Here’s the 2023 CBEST thematic report.
CBEST Red Teaming with SECFORCE
SECFORCE is a CBEST and CREST-approved penetration testing provider.
Contact us today if you’re looking for a reliable partner to help you with your CBEST assessment.
You may also be interested in...
Follow these signs to ensure your Red Team vendor is a match for your organisation.
See more
We don’t think the standard approach of modifying commercial C2s to evade detection will be sustainable for much longer. Artefacts of the original software will always create signatures, and as heuristics improve, those signatures will trigger detections. That's why we developed our own C2.
See more