GDPR, CRA, NIS, DORA, NIS2… Read enough cyber acronyms, and your eyes will start getting heavy. Although you might have acronym fatigue, DORA and NIS2 are on track to be two of the most important security legislative instruments in history.
And they do not mean the same thing.
If both DORA and NIS2 intersect with what your organisation does, understanding DORA vs NIS2 will be one of the most critical compliance questions you will face in the medium-term future.
Based on conversations with SECFORCE’s compliance experts, this blog post compares NIS2 and DORA.
The Biggest Difference between NIS2 and DORA
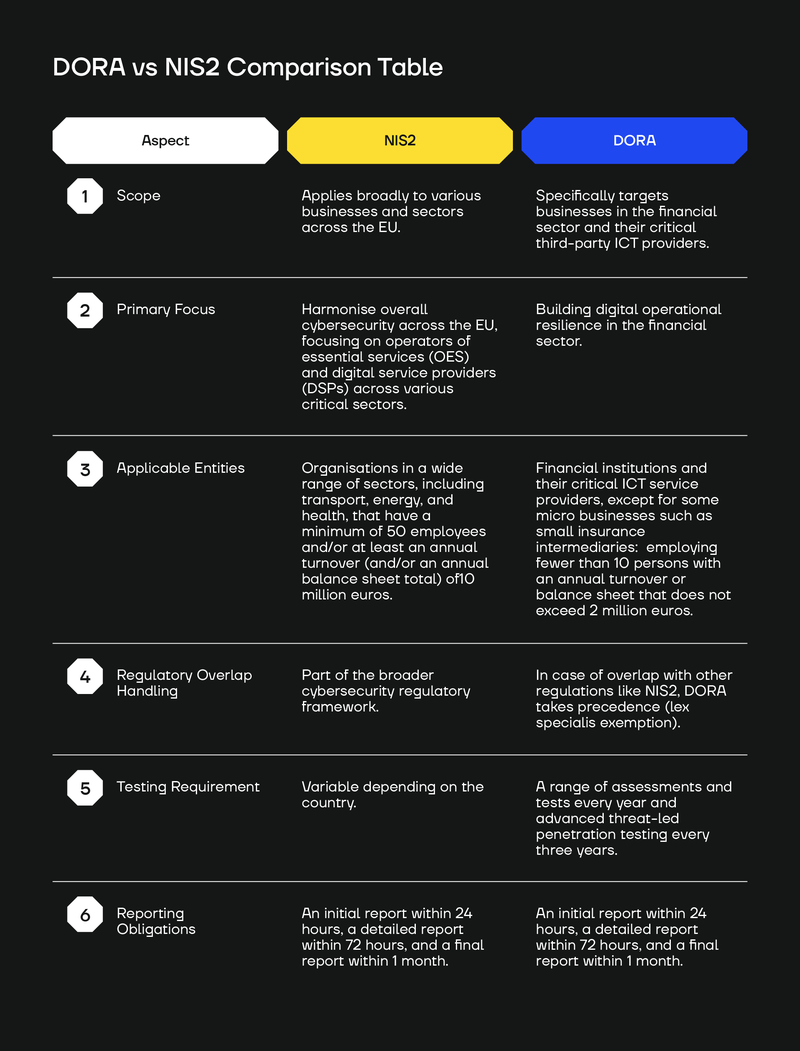
Network and Information Security Directive or NIS2 (Directive (EU) 2022/2555) is a directive, whereas the Digital Operational Resilience Act or DORA (EU Regulation No. 2022/2554) is a sector-specific regulation.
While NIS2 sets out cybersecurity standardisation goals that organisations based in all EU countries must achieve, it’s up to each EU country to “transpose” (a.k.a. “translate”) the NIS2 directive into actual national laws. This will happen at different times in different countries and through a variety of legislation.
In some countries, such as Hungary, bringing NIS2 into national law will only require amendments to existing legislation that almost fully transposes NIS2 already. In others, like Poland and Denmark, NIS2 will need totally new pieces of legislation and/or executive orders.
All the same, many parts of NIS2, such as the maximum fine of €10 million for breaches (or % of the global annual revenue, whichever is higher), will be similar everywhere.
DORA, on the other hand, is a finance sector-specific EU-wide regulation. It has a list of EU-wide compliance obligations that organisations within the scope will share regardless of where they are based. It also comes into force for every affected organisation at the same time (January 17, 2025)
Under DORA, a bank in one country - say France - and an investment firm in another country - for example, Germany - will need to meet the same compliance requirements. The only difference will be who their competent authority is going to be.
In this regard, local regulators are responsible for defining which organisations are critical, and therefore subjected to advanced testing requirements. The selection criteria they use however will be written within the DORA regulation, and not an arbitrary choice.
For the financial services industry, DORA Supersedes NIS2
Question: NIS2 and DORA have a lot of overlap, but if you are a financial services firm, which one applies to you?
Answer: DORA.
If your organisation could be described as a financial services firm, the most critical thing you need to understand when it comes to NIS2 versus DORA is a legal term called “lex specialis”
This means that if two laws cover the same thing, a law governing a specific subject matter is more important than a law governing only general matters.
So if DORA and NIS2 both apply to your organisation (which can happen), lex specialis prevails, and the sector-specific law (DORA) takes precedence over the more general regulation (NIS2) when it comes to any specific requirement.
Article 1.5.4 of the DORA act states that:
The proposal would not impact the NIS Directive but rather build on it and address possible overlaps via a lex specialis exemption. The interaction between the financial services regulation and the NIS Directive would continue to be governed by a lex specialis clause, thus exempting financial entities from substantive requirements in the NIS Directive and avoiding overlaps between the two acts. In addition, the proposal is consistent with the European Critical Infrastructure (ECI) Directive, currently under revision to enhance the protection and resilience of critical infrastructure against non-cyber threats.
So, if you are a:
- Bank
- Investment firm
- Insurance company
- Reinsurance company
- Payment institution
- Electronic money institution
- Crypto-asset service provider
- Credit rating agency
- Statutory auditor
- Audit firm
- Administrator of critical benchmark
- ICT third-party service provider
- Or any other financial entity covered by DORA and NIS2
Then you need to focus on complying with DORA above any national-level transposition of NIS2. For FSI cybersecurity risk management and reporting obligations, DORA is what counts.
DORA Is “Tougher” Than NIS2
DORA and NIS2 overlap a lot. For example, NIS2 has reporting timelines similar to DORA (24 and 72 hours) and equally large fines.
The two pieces of legislation are also designed to be systematically linked in terms of information sharing.
However, in almost every case, complying with DORA will take more work from your organisation than complying with NIS2.
To see why, look at how current adaptations of NIS2 compare to DORA.
Every national implementation of NIS2 will require organisations within the scope to deploy a broad suite of proactive security controls like multi-factor authentication and vulnerability management.
However, current drafts of NIS2 implementation laws, such as Germany’s “New Draft BSIG”, do not mandate offensive security measures such as penetration testing specifically, although organisations may be required to do comprehensive security testing in some cases.
DORA goes further by mandating a comprehensive digital operational resilience testing programme, which can include a range of assessments, tests, practices, methodologies, and tools and must happen yearly.
Additionally, DORA requires advanced testing through “threat-led penetration testing” every three years.
Learn more about DORA implementation requirements in this blog
DORA also places much more emphasis on managing risks related to critical ICT third-party service providers and will require impacted organisations to redesign a lot of their service contracts.
DORA vs NIS2 Comparison Table
DORA Compliance with SECFORCE
To help you become DORA compliant rapidly and sustainably, SECFORCE offers an end-to-end DORA compliance consultancy service that pairs our FSI compliance experts with your internal team to bring you honest, independent gap analysis and DORA compliance strategy.
Contact us to learn more.