Network pen testing identifies all the vulnerabilities affecting a particular infrastructure and exploits them (individually or in combination) to assess business impact. It shows you how far someone attacking your network could get.
In this blog post, we cover the different kinds of network pen testing, some of the most common misconceptions surrounding network testing, and must-know information for anyone considering whether it is right for their organisation.
What Is Network Pen Testing?
A network pen test is a cybersecurity exercise used to identify, exploit, and evaluate the security vulnerabilities within network infrastructure.
Network penetration testing is sometimes also called “infrastructure testing" because the majority of the time, what's being tested are the systems supporting and connected to a network.
However, to keep things simple, we can describe the testing of all network-related assets simply as network testing. This term can be further divided into two main network testing approaches: external and internal.
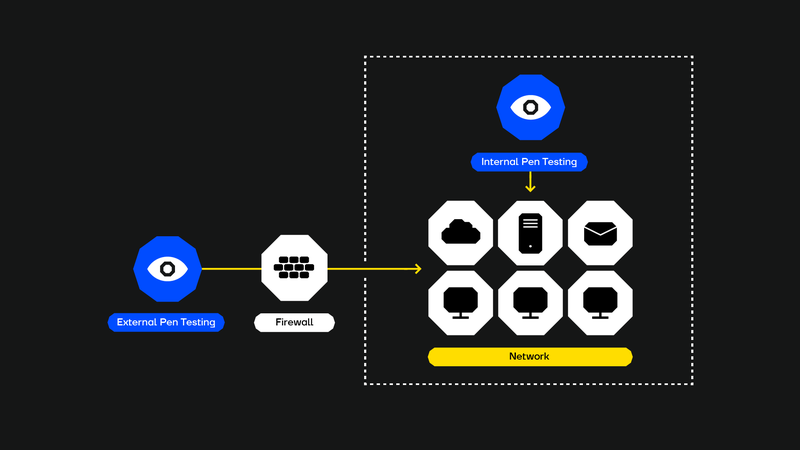
External network pen testing
External network penetration testing focuses on evaluating the security of an organisation’s externally exposed infrastructure—systems and services that are usually intentionally made accessible from the internet to meet business requirements. For example, websites, email servers, VPN endpoints, etc.
An external network pen test is usually conducted from a black-box/closed-box perspective, meaning the tester has no internal knowledge (like passwords or the inner workings of the systems).
The tester approaches the network like anyone coming from the internet would be able to.
Practically speaking, testing the network from the outside in means that external network testing can happen remotely.
Internal network pen testing
During internal network penetration testing, the focus is on evaluating the security of systems and infrastructure that are only accessible within the organisation’s internal environment. Systems like file servers, employee workstations, internal application servers, and Active Directory networks.
Internal network testing emulates the scenario of an attacker situated inside the corporate network.
This attacker could be a disgruntled or compromised employee. It could also be someone who just walked through your office door and plugged their laptop into a network port or logged into a guest wifi account (attacks like the one which recently compromised public wifi networks at several UK train stations).
Whatever the starting point, internal network testing answers one important question: If someone gains access to your internal network, what can they do? How far can they go? And if so, how?
Typically, internal network testing requires a tester to be present in an organisation's physical environment, such as its offices or a data centre.
However, during the COVID-19 lockdown period of 2020/2021, SECFORCE developed a novel solution for internal network testing that doesn’t require a tester to be onsite.
We built a device that we send to the organisation being tested, which they then plug into their internal network, allowing us to connect to their network remotely and securely, and perform an internal pen test.
Remote pen testing with SECFORCE’s solution
SECFORCE’s remote device is a small (but powerful) compact mini ITX board that connects via wireless and/or multiple/single Ethernet(s) to the organisation’s network. The connection back to SECFORCE headquarters is then established by following highly secure standards.
The device provides all the tools and utilities normally required by SECFORCE’s pen testing personnel in a single box. Through it, remote SECFORCE testers get the same control as if they were physically present in a network location.
Our security measures guarantee that connecting the SECFORCE remote pen testing device to a network will not increase the potential attack surface of the organisation being tested in any way.
Today, in a post-COVID world, many companies still benefit from this SECFORCE innovation because it can eliminate the need to pay for travel and accommodation costs for a tester and thus reduce network pen testing costs.
Should you do external or internal network pen testing?
Both external and internal network testing emulate different scenarios, so there isn’t an either/or question when choosing between them.
In our team’s opinion, organisations should do both external and internal network penetration tests regularly.
Network pen testing goes far beyond vulnerability scanning
Vulnerability scanning is not the same as network pen testing. Our blog post, "Penetration testing vs. vulnerability scanning," explores this common misconception in greater detail.
With vulnerability scanning, internal security teams or external vendors run a tool to identify certain types of vulnerabilities (e.g., missing patches) and then, hopefully, conduct more investigations later to eliminate false positives and determine the risk associated with these vulnerabilities.
A vulnerability assessment is always much less comprehensive than a network penetration test.
During a network penetration test, attempts will be made to escalate privileges. There won't be destructive actions or disruption of services, but ideally, there will be realistic attempts at exploiting vulnerable systems.
The outcome of a network pen test is a realistic appraisal of where a network is vulnerable and a pathway to remediation.
Bottom line:
- A vulnerability assessment enumerates vulnerabilities that may or may not enable attacks.
- A network pen test shows real exploitation pathways that attackers might use if a system is compromised.
Network penetration testing is not stealthy (unlike red teaming)
Internal or external network penetration testing is always done within the visibility of the organisation being tested. Stealth is never a feature of network penetration testing.
The purpose of network testing is to find all the vulnerabilities affecting the network infrastructure. To do so, the tester needs to be able to run “noisy”–but non-destructive–attacks such as port scanning or vulnerability scanning.
What will happen during a network penetration test:
- All of the vulnerabilities affecting the network infrastructure will be identified.
- We will attempt to compromise systems within the network (with permission).
- We will attempt to escalate privileges where applicable.
- We will leverage access obtained to target other systems in scope (as an attacker would).
What won't’ happen during a network penetration test:
- Attempts to remain stealthy.
- Destructive actions/disruption of services.
Read our “Pen Testing Versus Red Teaming Use Cases: We Asked the Experts” blog post to learn more about the difference between the two.
When Should You Do Network Pen Testing?
Regularly.
If an attacker targets a mail server, they could potentially gain access to everyone's emails in the organisation.
In most organisations, there are potentially hundreds of other critical network assets, like a virtual private network (VPN) system that allows users to connect to the internal network over the internet.
The more exposed a network system is, and the more sensitive the data it stores or processes, the more regularly you should test it.
In our team’s experience, network penetration testing doesn't stop being important at a certain level of security maturity. Don’t stop testing for exploitation pathways because you’ve improved at detecting and preventing attacks.
It’s easy for an organisation to rely too heavily on detecting and blocking attacks rather than addressing the underlying vulnerabilities. This strategy leaves the risk of detection bypass open.
Our team recommends approaching network pen testing as a continuous security validation and risk reduction process.
How to Make the Most of Network Pen Testing
Here are some tips from our team on making the most of a network penetration test.
Before the network pen test
Define the scope and communication protocols
- Share details such as which network ranges are in scope and provide written approvals from any third-party hosting systems in scope.
- Collaborate with the pentesting provider to answer any questions they might have, as those are there to help the engagement go smoothly.
- Define points of contact for the engagement and agree on a secure communication channel.
Handle access requirements in advance
- External testing may require allow-listing the testing team’s IPs.
- For external testing, where possible, allow the testing team to verify access one or two days before the test starts to allow time to solve access issues without eating away testing time.
- For internal testing, ensure physical access to necessary facilities (e.g., office buildings, data centres) is prearranged to avoid delays.
- For internal testing, ensure the tester (or SECFORCE’s remote testing device) will be connected to the right network point from which they can access all the systems/ranges in scope.
Prepare your environment
- Patch systems before the pen test. This will prevent the report from featuring potentially hundreds of vulnerabilities that could have been addressed with routine updates.
- Inform your SOC or relevant team about the test to prevent it from being treated as a security incident.
Anticipate higher than normal computational and storage impact from logging
- Penetration testing can generate significant logs. Ensure your systems have sufficient disk space to handle the increased logging activity to avoid system disruptions.
During the network pen test
- Keep communication lines open. After designating a point of contact between your team and the testers, make sure they are reachable during testing hours.
- Address issues quickly, like access errors, downtime, or other disruptions, to keep the test on track.
After the network pen test
- Read the report, or at least the sections relevant to you (e.g., the Executive Summary if you’re a C-level stakeholder to understand the business-critical issues and their potential impact and the technical sections if you’re part of the technical team to see how the vulnerabilities were exploited, what attackers could achieve, and the recommended fixes).
- Create a realistic remediation plan. Report recommendations will provide guidance about proper mitigation, but you will need to assign responsibilities and deadlines to the appropriate teams while considering their skill sets. Ensure the fixes address root causes and are implemented in a way that genuinely reduces risk.
- Validate your remediation efforts by scheduling a retest. Retesting is typically quick and focuses on verifying that previous vulnerabilities have been properly addressed.
Doing the above can help ensure a more efficient and effective pen test.
Network Pen Testing with SECFORCE
Our team has deep expertise in network penetration testing, including writing custom network testing tools, which we are pleased to say have gained traction in the wider offensive security community.
The SECFORCE team are network penetration testing experts. We work with companies of all different sizes, budgets, and sectors.
Contact us for an appraisal of your testing needs.